

User Controls
An Unresponsive Port
-
2016-02-07 at 7:26 AM UTCI have a port on a device that is open but it wont give me any response when I connect to it and wont give me any response when I send it random data.
The port number is a high number with no know default protocol.
What are my options? -
2016-02-07 at 9:39 AM UTCThe port is 5502 - [FONT=Helvetica][SIZE=12px]Radio Free Ethernet
What can I do now that I know it's open?[/SIZE][/FONT] -
2016-02-07 at 11:58 AM UTC
-
2016-02-07 at 12:13 PM UTCThis is super interesting. All I could find on short notice is this (from nmap docs): https://nmap.org/book/vscan.html
I'll look more into this soon as I've had this problem a few times before. -
2016-02-07 at 2:47 PM UTCSome honeypots also present what appear to be open ports, but your IP and infos are merely being logged. The port will not accept any commands.
-
2016-02-07 at 4:05 PM UTC
The port is 5502 - [FONT=Helvetica][SIZE=12px]Radio Free Ethernet
What can I do now that I know it's open?[/SIZE][/FONT]
According to this page http://www.networksorcery.com/enp/protocol/ip/ports05000.htm the port is usually implicated in the FCP protocol, FirstClass Protocol, which is a nifty type of old school transport layer networking protocol.
https://en.wikipedia.org/wiki/FirstClass#FCP.2C_the_FirstClass_Protocol
I'd say, craft a FCP packet and fire it at the port and see what happens?
Also, obviously it could be something entirely unrelated, this is just based off of what this first site is telling me. -
2016-02-08 at 7:29 AM UTC
Some honeypots also present what appear to be open ports, but your IP and infos are merely being logged. The port will not accept any commands.
Sending traffic to an open port wouldn't constitute breaking the law in most places I believe. If it did, even pinging that machine or sending it tcp syn packets (for port scanning) would be a violation.
That said, good point. I'd use a vpn or proxychains + tor for this kinda stuff.
<tin foil hat> -
2016-02-08 at 12:57 PM UTC
Sending traffic to an open port wouldn't constitute breaking the law in most places I believe. If it did, even pinging that machine or sending it tcp syn packets (for port scanning) would be a violation.
That said, good point. I'd use a vpn or proxychains + tor for this kinda stuff.
<tin foil hat>
Many sys admins consider even a passive port scan to be a legitimate attack. You'd be shocked at how anal and offense-orientated they are. They figure, why the fuck would you even be scanning their network in the first place? So although it's not a crime to scan networks, many network administrators just want to know who you are anyways. So they set up dummy ports that have no server on them just to log the IPs which try to scan them. But it's not hard to just use a mule machine and bounce scans off that, either pipe the results somewhere else or pick it up later, keep switching mules every session. -
2016-02-08 at 5:18 PM UTC
Many sys admins consider even a passive port scan to be a legitimate attack. You'd be shocked at how anal and offense-orientated they are. They figure, why the fuck would you even be scanning their network in the first place? So although it's not a crime to scan networks, many network administrators just want to know who you are anyways. So they set up dummy ports that have no server on them just to log the IPs which try to scan them. But it's not hard to just use a mule machine and bounce scans off that, either pipe the results somewhere else or pick it up later, keep switching mules every session.
Maybe medium or large companies have that kind of sysadmins as well as honeypots and ids'. All the start ups I know don't spend a single minute thinking about this stuff. Then they get big. Then they lose 30mln customer records to bobby tables.
Anyways, OP, any luck? -
2016-02-08 at 8:11 PM UTCI read an article somewhere that was about some guy that was port scanning his local police station or something and they knew about it for a while. He got arrested but I'm not sure if it was for the port scans.
Anyways, not to let everyone down, but this is a device that I actually own that I'm doing this with. I'm just curious about what this port is doing open.
The device is a VirginMobile Mingle Hotspot, model "AirCard 778S". I got it for free a while back and was going to use it for anonymous internet use via fake details and TOR, but since then the price plans have changed and it's better to just get a prepaid phone, root it, and use that for internet.
Anyways, to get the the advanced menu, a MSL(master subsidy lock) code is needed(six digits I believe, possible characters). I tried a bunch at random and didn't get locked out so I made a Android program that would brute force "000000" through "999999". But when I ran it, it eventually did turn out that there was a limit on the number of passwords.
So, I turned on Burp Suite and begin looking through the source code, and found a JavaScript file that had the last part of the link that I needed. I put the link in my browser, pressed enter, and volla, I'm in the advance menu.
This is part of the JavaScript file, I coundn't post the whole thing because the max char limit here is 100,000...
function ready() {
sierra = new SierraData({
"session": {
"userRole": "Admin",
"lang": "en",
"secToken": "IxgZ0sdnUTnzpbtafCVTF7nXW0saBGZ"
},
"general": {
"defaultLanguage": "en"
}
});
sierraUI = new SierraUI();
sierraForm = new SierraForm();
function SprintNetworkSetupUIModule() {
var _model;
var _ui;
var initialized = false;
var $buttonUpdatePrl;
var $buttonUpdateDataProfile;
var $buttonUICCUnlock;
var $buttonActivateSprintDatalink;
var $buttonActivationCancel;
var $buttonAdvancedSettings;
var $buttonSPCunlock;
var $buttonSPCcancel;
var $buttonClosePrlSuccess;
var $buttonClosePrlError;
var $SPCform;
var $SPCinput;
var $networkButtons;
var $navVMLink;
var $navCarrierUsage;
var $navMyAccount;
var $messageWaitConnection;
var $dialogActivationPlan;
var $navVM;
var SPCunlockInProgress;
var lastSessionState;
var lastSessionType;
var sessionCanceled = false;
var almostDoneActive = true;
function _handleButtonActivationCancel(e) {
sessionCanceled = true;
sierra.submitRequest( new SierraRequest({
'data': {'oma.sprint.cancel': 1}
}));
_ui.closeDialog();
}
function _handleButtonUpdatePrl(e) {
sierra.submitRequest( new SierraRequest({
'data': {'oma.sprint.start' : 'PRL'} // PRL
}));
}
function _handleButtonUpdateDataProfile(e) {
sierra.submitRequest( new SierraRequest({
'data': {'oma.sprint.start': 'DC'}
}));
}
function _handleButtonUICCUnlock(e) {
sierra.submitRequest( new SierraRequest({
'data': {'oma.sprint.start': 'SIMUNLOCK'}
}));
}
function _handleSessionState() {
var sessionState = sierra.get('oma.sprint.sessionState');
var lastSessionTypeStart = sierra.get('oma.sprint.lastSessionTypeStart');
var lastSessionResult = sierra.get('oma.sprint.lastSessionResult');
var successAtemptCount = sierra.get("dsa.successAttemptCount");
var generalActivated = sierra.get("general.activated");
if($dialog_OobScreen && _.hasClass($dialog_OobScreen, "active") && generalActivated){
_ui.closeDialog();
almostDoneActive = true;
return false;
}
if(sierra.get('general.TCAaccepted') === true && almostDoneActive){
switch(sessionState) {
case 'Idle':
if(sessionCanceled) {
_ui.closeDialog();
if(lastSessionTypeStart === 'PRL') {
_ui.dialog({'type': 'PrlError'});
}
sessionCanceled = false;
}
else if(lastSessionState && lastSessionState !== 'Idle') {
if(lastSessionTypeStart === 'PRL') {
/* Set a wait to handle out or order events from FW for a canceled session */
setTimeout(function(){
_ui.closeDialog();
if (sierra.get('oma.sprint.lastSessionResult') == 0) {
_ui.dialog({'type': 'PrlSuccess'});
}
else {
_ui.dialog({'type': 'PrlError'});
}
},4000);
}
else if (lastSessionTypeStart === 'HFAFUMO' && (lastSessionResult == 0 || lastSessionResult == 32533)) {
_ui.dialog({'type': 'ActivationPlan','locked': true });
almostDoneActive = false;
}
else{
if(($dialog_OobScreen && $dialog_OobScreenProgress) && (!_.hasClass($dialog_OobScreen, "active") && !_.hasClass($dialog_OobScreenProgress, "active"))){
_ui.closeDialog();
}
}
}
break;
case 'Pending':
case 'Active':
//handle immediate NI session that follows HFA FUMO and IDLE status is skipped
//Can only get here if AP dialog not opened
if(lastSessionType && lastSessionType === 'HFAFUMO' && lastSessionTypeStart === "NI") {
//ignore this session and show Activation Plan
_ui.dialog({'type': 'ActivationPlan','locked': true });
almostDoneActive = false;
return false;
}
if(successAtemptCount > 0 || generalActivated === true) {
_ui.dialog({'type': 'Activation','locked': true });
}
else {
_ui.dialog({'type': 'OobScreen', 'locked': true});
}
break;
}
}
lastSessionState = sessionState;
lastSessionType = lastSessionTypeStart;
}
function _handleButtonActivateSprintDatalink(e) { _showSPCform('manual'); }
function _handleButtonAdvancedSettings(e) { _showSPCform('advanced'); }
function _handleSPClockStatus() {
switch(sierra.get('general.SPClockStatus')) {
/*case 'NoRequest':*/
case 'SPCLocked':
_ui.dialog({'type': 'SPCInvalid'});
break;
case 'MaxSPCRetries':
_ui.dialog({'type':'SPCMaxRetries'});
break;
}
}
function _handleButtonSPCunlock(e) {
SPCunlockInProgress = $SPCform.attr('class');
sierra.submitRequest( new SierraRequest({
'data': {'general.SPCunlock' : $SPCinput.val()},
'error': function() {
_hideSPCform();
SPCunlockInProgress = null;
setTimeout(_handleSPClockStatus,3000);
},
'success': function() {
switch(SPCunlockInProgress) {
case 'advanced':
window.location.hash = [B]'#settings/network/advanced'[/B];
break;
case 'manual':
window.location.hash = [B]'#settings/network/manual'[/B];
break;
}
SPCunlockInProgress = null;
}
}));
_hideSPCform();
}
Here are pictures of the advanced menus. In the second one, I can change the 3g setting and save it, but when I fill in the feilds for the 4g settings and click 'submit', I get an error.
I have no idea what these setting are for. As far as the port goes, I still have gotten a response from it.
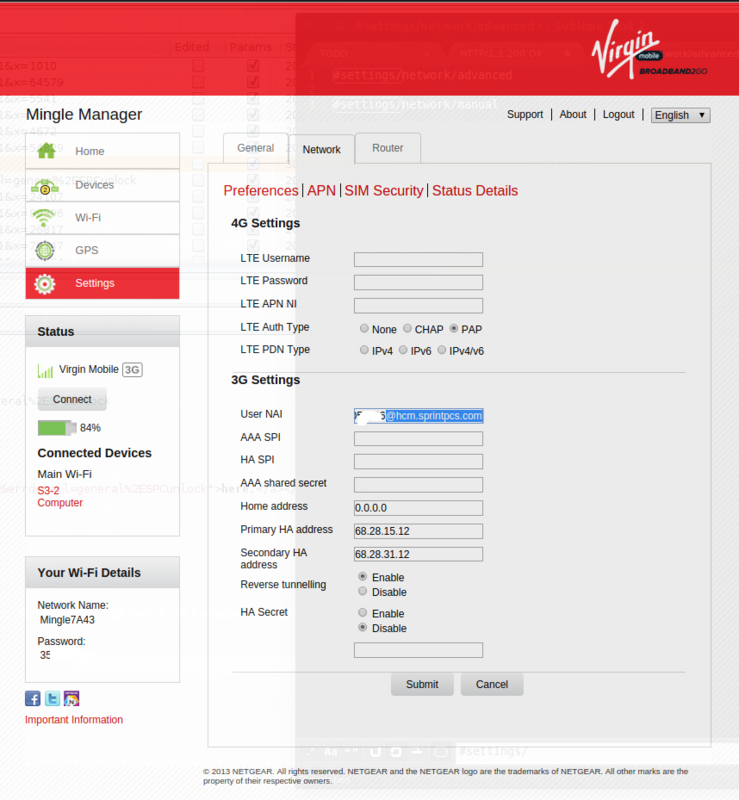
-
2016-02-08 at 9:57 PM UTC
As far as the port goes, I still have gotten a response from it.
Have you tried pinging it, and if so, did it reply? Try to Telnet into it to see if you get any return. -
2016-02-09 at 12:02 AM UTC
Have you tried pinging it, and if so, did it reply? Try to Telnet into it to see if you get any return.
Pinging a port...?
I have tried connecting to it via a socket and it connects, so it's open. The ports that it has open are 53, 80, 443, and 5502. RIght now my port scanner basically just attemps to connect a raw socket to a port, with a set timeout, and if it conencts, then it closes it and list it as open. If the connection is refused, then it lists it as closed.
I've to Telnet and SSH and I get no response. No response for anything, except for port 80 and 443. Port 443 is weird, because everything I do on via the normal browser is HTTP on port 80 and never goes to SSL. I have no idea where it is suppose to use SSL as I've been through all of the pages that I can access normally. It's a tricky little thing. -
2016-02-09 at 12:22 AM UTC
-
2016-02-09 at 12:51 AM UTCall paping is going to do is test connection establishment, won't tell you anything about the service
the only real way to get anything out of it is to try and guess what protocol it expects and throw data at it until it responds - first thing I'd try is just send some linefeeds via tcp then udp if you get no response, then as sophie suggested, try to guess the service based on the port and send a command in that protocol to see if you get a response. it might be worth using wireshark or tcpdump to inspect the initial connection, as the connect response from the server may give clues as to what the service is. -
2016-02-09 at 12:54 AM UTChttp://www.iana.org/assignments/service-names-port-numbers/service-names-port-numbers.txt
IANA keeps an official list of services that use specific ports; yours is assigned to FCP, an old Cisco wrapper for iSCSI I think. just skimmed over this: http://www.ciscopress.com/articles/article.asp?p=484553&seqNum=2. -
2016-02-09 at 2:19 AM UTC
C:> paping www.google.com -p 5502 -c 4
https://code.google.com/archive/p/paping/all paping is going to do is test connection establishment, won't tell you anything about the service
Wouldn't this be the same as opening up a raw socket connection? I had actually came across Paping when searching for "pinging a port". I searched because it didn't really make sense to me.the only real way to get anything out of it is to try and guess what protocol it expects and throw data at it until it responds - first thing I'd try is just send some linefeeds via tcp then udp if you get no response, then as sophie suggested, try to guess the service based on the port and send a command in that protocol to see if you get a response. it might be worth using wireshark or tcpdump to inspect the initial connection, as the connect response from the server may give clues as to what the service is.
I've tried connecting and sending line feeds via a raw socket but I believe it's TCP/IP and not UDP. What type of socket am I using if I'm using the below java code...
s = new Socket();
s.bind(new InetSocketAddress("0.0.0.0", 5555));
s.connect(new InetSocketAddress(new InetSocketAddress("192.168.1.2", 5502)), 5000);
outputStream = new PrintWriter(s.getOutputStream(), true);
inputStream = new BufferedReader(new InputStreamReader(s.getInputStream()));
...
...
... -
2016-02-09 at 2:46 AM UTCyeah, about paping that's right, instead of sending data like an icmp ping, it sends connect requests and logs how long they take and whether they succeed or not. won't tell you anything about the expected protocol.
read my second post; it looks to be a cisco-specific protocol relating to network storage.
for your code, I'm pretty sure that's just a java wrapper for sockets/winsock so it'll be connecting via tcp unless specified otherwise. -
2016-02-12 at 8:04 AM UTC
I'd say, craft a FCP packet and fire it at the port and see what happens?
How can I do this?
I've come across this code that will(I've verified via TCPdump on one of my phones) send packets from my wireless card.
https://gist.github.com/austinmarton/1922600
#include <arpa/inet.h>
#include <linux/if_packet.h>
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
#include <sys/ioctl.h>
#include <sys/socket.h>
#include <net/if.h>
#include <netinet/ether.h>
#define MY_DEST_MAC0 0x00
#define MY_DEST_MAC1 0x00
#define MY_DEST_MAC2 0x00
#define MY_DEST_MAC3 0x00
#define MY_DEST_MAC4 0x00
#define MY_DEST_MAC5 0x00
#define DEFAULT_IF "wlan0"
#define BUF_SIZ 1024
int main(int argc, char *argv[])
{
int sockfd;
struct ifreq if_idx;
struct ifreq if_mac;
int tx_len = 0;
char sendbuf[BUF_SIZ];
struct ether_header *eh = (struct ether_header *) sendbuf;
struct iphdr *iph = (struct iphdr *) (sendbuf + sizeof(struct ether_header));
struct sockaddr_ll socket_address;
char ifName[IFNAMSIZ];
/* Get interface name */
if (argc > 1)
strcpy(ifName, argv[1]);
else
strcpy(ifName, DEFAULT_IF);
/* Open RAW socket to send on */
if ((sockfd = socket(AF_PACKET, SOCK_RAW, IPPROTO_RAW)) == -1) {
perror("socket");
}
/* Get the index of the interface to send on */
memset(&if_idx, 0, sizeof(struct ifreq));
strncpy(if_idx.ifr_name, ifName, IFNAMSIZ-1);
if (ioctl(sockfd, SIOCGIFINDEX, &if_idx) < 0)
perror("SIOCGIFINDEX");
/* Get the MAC address of the interface to send on */
memset(&if_mac, 0, sizeof(struct ifreq));
strncpy(if_mac.ifr_name, ifName, IFNAMSIZ-1);
if (ioctl(sockfd, SIOCGIFHWADDR, &if_mac) < 0)
perror("SIOCGIFHWADDR");
/* Construct the Ethernet header */
memset(sendbuf, 0, BUF_SIZ);
/* Ethernet header */
eh->ether_shost[0] = ((uint8_t *)&if_mac.ifr_hwaddr.sa_data)[0];
eh->ether_shost[1] = ((uint8_t *)&if_mac.ifr_hwaddr.sa_data)[1];
eh->ether_shost[2] = ((uint8_t *)&if_mac.ifr_hwaddr.sa_data)[2];
eh->ether_shost[3] = ((uint8_t *)&if_mac.ifr_hwaddr.sa_data)[3];
eh->ether_shost[4] = ((uint8_t *)&if_mac.ifr_hwaddr.sa_data)[4];
eh->ether_shost[5] = ((uint8_t *)&if_mac.ifr_hwaddr.sa_data)[5];
eh->ether_dhost[0] = MY_DEST_MAC0;
eh->ether_dhost[1] = MY_DEST_MAC1;
eh->ether_dhost[2] = MY_DEST_MAC2;
eh->ether_dhost[3] = MY_DEST_MAC3;
eh->ether_dhost[4] = MY_DEST_MAC4;
eh->ether_dhost[5] = MY_DEST_MAC5;
/* Ethertype field */
eh->ether_type = htons(ETH_P_IP);
tx_len += sizeof(struct ether_header);
/* Packet data */
sendbuf[tx_len++] = 0xde;
sendbuf[tx_len++] = 0xad;
sendbuf[tx_len++] = 0xbe;
sendbuf[tx_len++] = 0xef;
/* Index of the network device */
socket_address.sll_ifindex = if_idx.ifr_ifindex;
/* Address length*/
socket_address.sll_halen = ETH_ALEN;
/* Destination MAC */
socket_address.sll_addr[0] = MY_DEST_MAC0;
socket_address.sll_addr[1] = MY_DEST_MAC1;
socket_address.sll_addr[2] = MY_DEST_MAC2;
socket_address.sll_addr[3] = MY_DEST_MAC3;
socket_address.sll_addr[4] = MY_DEST_MAC4;
socket_address.sll_addr[5] = MY_DEST_MAC5;
/* Send packet */
if (sendto(sockfd, sendbuf, tx_len, 0, (struct sockaddr*)&socket_address, sizeof(struct sockaddr_ll)) < 0)
printf("Send failed\n");
return 0;
}
I'm not sure what to change in the code though as I'm a novice with C. This is the type of stuff I'm going to learn though. Lower level C code, mostly TCP/IP.
Anyways, the packet data is going to be "222.173.190.239"(deadbeef) but I really don't know what to make it and don't know what to make the headers... -
2016-02-14 at 4:54 PM UTC
How can I do this?
I've come across this code that will(I've verified via TCPdump on one of my phones) send packets from my wireless card.
https://gist.github.com/austinmarton/1922600
#include <arpa/inet.h>
#include <linux/if_packet.h>
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
#include <sys/ioctl.h>
#include <sys/socket.h>
#include <net/if.h>
#include <netinet/ether.h>
#define MY_DEST_MAC0 0x00
#define MY_DEST_MAC1 0x00
#define MY_DEST_MAC2 0x00
#define MY_DEST_MAC3 0x00
#define MY_DEST_MAC4 0x00
#define MY_DEST_MAC5 0x00
#define DEFAULT_IF "wlan0"
#define BUF_SIZ 1024
int main(int argc, char *argv[])
{
int sockfd;
struct ifreq if_idx;
struct ifreq if_mac;
int tx_len = 0;
char sendbuf[BUF_SIZ];
struct ether_header *eh = (struct ether_header *) sendbuf;
struct iphdr *iph = (struct iphdr *) (sendbuf + sizeof(struct ether_header));
struct sockaddr_ll socket_address;
char ifName[IFNAMSIZ];
/* Get interface name */
if (argc > 1)
strcpy(ifName, argv[1]);
else
strcpy(ifName, DEFAULT_IF);
/* Open RAW socket to send on */
if ((sockfd = socket(AF_PACKET, SOCK_RAW, IPPROTO_RAW)) == -1) {
perror("socket");
}
/* Get the index of the interface to send on */
memset(&if_idx, 0, sizeof(struct ifreq));
strncpy(if_idx.ifr_name, ifName, IFNAMSIZ-1);
if (ioctl(sockfd, SIOCGIFINDEX, &if_idx) < 0)
perror("SIOCGIFINDEX");
/* Get the MAC address of the interface to send on */
memset(&if_mac, 0, sizeof(struct ifreq));
strncpy(if_mac.ifr_name, ifName, IFNAMSIZ-1);
if (ioctl(sockfd, SIOCGIFHWADDR, &if_mac) < 0)
perror("SIOCGIFHWADDR");
/* Construct the Ethernet header */
memset(sendbuf, 0, BUF_SIZ);
/* Ethernet header */
eh->ether_shost[0] = ((uint8_t *)&if_mac.ifr_hwaddr.sa_data)[0];
eh->ether_shost[1] = ((uint8_t *)&if_mac.ifr_hwaddr.sa_data)[1];
eh->ether_shost[2] = ((uint8_t *)&if_mac.ifr_hwaddr.sa_data)[2];
eh->ether_shost[3] = ((uint8_t *)&if_mac.ifr_hwaddr.sa_data)[3];
eh->ether_shost[4] = ((uint8_t *)&if_mac.ifr_hwaddr.sa_data)[4];
eh->ether_shost[5] = ((uint8_t *)&if_mac.ifr_hwaddr.sa_data)[5];
eh->ether_dhost[0] = MY_DEST_MAC0;
eh->ether_dhost[1] = MY_DEST_MAC1;
eh->ether_dhost[2] = MY_DEST_MAC2;
eh->ether_dhost[3] = MY_DEST_MAC3;
eh->ether_dhost[4] = MY_DEST_MAC4;
eh->ether_dhost[5] = MY_DEST_MAC5;
/* Ethertype field */
eh->ether_type = htons(ETH_P_IP);
tx_len += sizeof(struct ether_header);
/* Packet data */
sendbuf[tx_len++] = 0xde;
sendbuf[tx_len++] = 0xad;
sendbuf[tx_len++] = 0xbe;
sendbuf[tx_len++] = 0xef;
/* Index of the network device */
socket_address.sll_ifindex = if_idx.ifr_ifindex;
/* Address length*/
socket_address.sll_halen = ETH_ALEN;
/* Destination MAC */
socket_address.sll_addr[0] = MY_DEST_MAC0;
socket_address.sll_addr[1] = MY_DEST_MAC1;
socket_address.sll_addr[2] = MY_DEST_MAC2;
socket_address.sll_addr[3] = MY_DEST_MAC3;
socket_address.sll_addr[4] = MY_DEST_MAC4;
socket_address.sll_addr[5] = MY_DEST_MAC5;
/* Send packet */
if (sendto(sockfd, sendbuf, tx_len, 0, (struct sockaddr*)&socket_address, sizeof(struct sockaddr_ll)) < 0)
printf("Send failed\n");
return 0;
}
I'm not sure what to change in the code though as I'm a novice with C. This is the type of stuff I'm going to learn though. Lower level C code, mostly TCP/IP.
Anyways, the packet data is going to be "222.173.190.239"(deadbeef) but I really don't know what to make it and don't know what to make the headers…
I'm pretty much a novice at C as well, but this is what i can tell you if you don't know already.
/* Open RAW socket to send on */
if ((sockfd = socket(AF_PACKET, SOCK_RAW, IPPROTO_RAW)) == -1) {
perror("socket");
}
AF_PACKET sets the domain to a packet socket. For instance if you want to set the domain to an IPv4 adress you'd use AF_INET. SOCKET_RAW sets the socket type to raw, which you should do if you're constructing your own ethernet header. If not SOCK_DGRAM can be used. And IPPROTO means just what you'd think it means, it has to do with the protocol, you could set it to IPPROTO_TCP or IPPROTO_UDP. If you haveto change anything i think it may be this or the packet data.
sendbuf[tx_len++] = 0xde;
sendbuf[tx_len++] = 0xad;
sendbuf[tx_len++] = 0xbe;
sendbuf[tx_len++] = 0xef;
No clue what this all means. It's so much easier in python though, for real python is awesome
import socket
target = "222.173.190.239"
port = 1337
# Packet data
data = 'f1a525da11f6'.decode('hex')
# Create socket object (IPv4 and UDP)
client = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
# Connect to client
client.connect((target, port))
# Send our data
client.send(data)
# Recieve our respone
response = client.recv(4046)
print response
I'm pretty sure this would work if you could find out what type of data an fcp packet sends and the neat thing about the fcp protocol is that it can work on different layers, like TCP/IP what let's th recieving end know it's a FCP packet is a special kind of identifier in the packet data if i do remember correctly. -
2016-02-14 at 6:32 PM UTC
And IPPROTO means just what you'd think it means, it has to do with the protocol, you could set it to IPPROTO_TCP or IPPROTO_UDP.
These are the other protocols I can use...
enum
{
IPPROTO_IP = 0, /* Dummy protocol for TCP. */
#define IPPROTO_IP IPPROTO_IP
IPPROTO_ICMP = 1, /* Internet Control Message Protocol. */
#define IPPROTO_ICMP IPPROTO_ICMP
IPPROTO_IGMP = 2, /* Internet Group Management Protocol. */
#define IPPROTO_IGMP IPPROTO_IGMP
IPPROTO_IPIP = 4, /* IPIP tunnels (older KA9Q tunnels use 94). */
#define IPPROTO_IPIP IPPROTO_IPIP
IPPROTO_TCP = 6, /* Transmission Control Protocol. */
#define IPPROTO_TCP IPPROTO_TCP
IPPROTO_EGP = 8, /* Exterior Gateway Protocol. */
#define IPPROTO_EGP IPPROTO_EGP
IPPROTO_PUP = 12, /* PUP protocol. */
#define IPPROTO_PUP IPPROTO_PUP
IPPROTO_UDP = 17, /* User Datagram Protocol. */
#define IPPROTO_UDP IPPROTO_UDP
IPPROTO_IDP = 22, /* XNS IDP protocol. */
#define IPPROTO_IDP IPPROTO_IDP
IPPROTO_TP = 29, /* SO Transport Protocol Class 4. */
#define IPPROTO_TP IPPROTO_TP
IPPROTO_DCCP = 33, /* Datagram Congestion Control Protocol. */
#define IPPROTO_DCCP IPPROTO_DCCP
IPPROTO_IPV6 = 41, /* IPv6 header. */
#define IPPROTO_IPV6 IPPROTO_IPV6
IPPROTO_RSVP = 46, /* Reservation Protocol. */
#define IPPROTO_RSVP IPPROTO_RSVP
IPPROTO_GRE = 47, /* General Routing Encapsulation. */
#define IPPROTO_GRE IPPROTO_GRE
IPPROTO_ESP = 50, /* encapsulating security payload. */
#define IPPROTO_ESP IPPROTO_ESP
IPPROTO_AH = 51, /* authentication header. */
#define IPPROTO_AH IPPROTO_AH
IPPROTO_MTP = 92, /* Multicast Transport Protocol. */
#define IPPROTO_MTP IPPROTO_MTP
IPPROTO_BEETPH = 94, /* IP option pseudo header for BEET. */
#define IPPROTO_BEETPH IPPROTO_BEETPH
IPPROTO_ENCAP = 98, /* Encapsulation Header. */
#define IPPROTO_ENCAP IPPROTO_ENCAP
IPPROTO_PIM = 103, /* Protocol Independent Multicast. */
#define IPPROTO_PIM IPPROTO_PIM
IPPROTO_COMP = 108, /* Compression Header Protocol. */
#define IPPROTO_COMP IPPROTO_COMP
IPPROTO_SCTP = 132, /* Stream Control Transmission Protocol. */
#define IPPROTO_SCTP IPPROTO_SCTP
IPPROTO_UDPLITE = 136, /* UDP-Lite protocol. */
#define IPPROTO_UDPLITE IPPROTO_UDPLITE
IPPROTO_RAW = 255, /* Raw IP packets. */
#define IPPROTO_RAW IPPROTO_RAW
IPPROTO_MAX
};
import socket
target = "222.173.190.239"
port = 1337
# Packet data
data = 'f1a525da11f6'.decode('hex')
# Create socket object (IPv4 and UDP)
client = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
# Connect to client
client.connect((target, port))
# Send our data
client.send(data)
# Recieve our respone
response = client.recv(4046)
print response
I don't know much about Python, but this looks like it's just a raw socket connection, which I already am doing in Java.