

User Controls
Everybody should start using radios instead of cell phones
-
2024-10-06 at 6:12 PM UTCMaybe have a cell phone or some kind of VOIP thing for home since you could be located and arrested and just use it in the car when you're moving around.
I was talking to somebody from Latin America and they said criminals there use radios. I said people would here if they weren't stupid. But they probably set up their own repeaters and all kinds of shit. Idk if you're supposed to have a licence to run a repeater, if so that would suck because it's something stationary that they can take. Ig you could find other legitimate ones and use them illegally.
The channels you don't need a licence for (MURS and FRS I believe) I read that information was collected from them whatever that means. The FCC sits there and transcribes everything? I think these are the channels programmed to walkie talkies. Regardless of what is recorded, the ability to do this would depend on transmit power.
Ig if you wanted to mitigate the risk of the FBI/Mossad turning them into bombs you could state that you were handing some of them at random out to inner city children of convicts who live in close proximity to synagogues. 🤡 Like a charity.
But this would be cool. There was a time we did it as kids but I would never want my own children playing on them. It's more dangerous than the internet.The following users say it would be alright if the author of this post didn't die in a fire! -
2024-10-06 at 6:19 PM UTCPeople could just use cell phones at home, or if you wanted to have a conversation about sex and jerk off in your car you could use the cell phone and know that it was only the FBI/NSA listening.
The whole point of licenses is that the government is so fucking paranoid they have to know who everybody is and what they were saying. I think they would freak out pretty good if everybody started doing this. Not just criminals. -
2024-10-06 at 6:24 PM UTCTheres really no point when online encrypted communications are so easy to use and readily available.
Radio signals can be tracked, listened in on, or transmitted over if you don't know what you're doing and most people don't. Not to mention, at least here in the US there are many HAM enthusiasts who are so old and ornery and have so much time on their hands they make speedy parker look young again, who can and will hunt you down and report you to the authorities for improper use of equipment.
Plus I'm sure any criminal organization (or any organization) probably isn't exclusively using radio signals for communication, it's likely just used to subsidize other methods of short distance communications (I.E. sensitive information is still likely communicated through encrypted messaging software) -
2024-10-06 at 6:34 PM UTCI agree. I stopped paying my phone bill and it has gone to collections, fuck those hebrews. I have been buying SDRs and HF receivers and trying to figure out how to assign a fax number to a web server instead of trying to get a new phone number. And learning the entire evil jedi magic underpinnings of the "PSTN" phone switch system how a SYSTEM decides how NUMBERS are ASSIGNED instead of being forced to use their corrupt system of "COUNTRY CALLING CODES" which is communist in nature and goes against other international technology associating like
https://en.wikipedia.org/wiki/T.38
https://en.wikipedia.org/wiki/Asterisk_(PBX)
https://en.wikipedia.org/wiki/FreeSWITCH
https://en.wikipedia.org/wiki/Telephony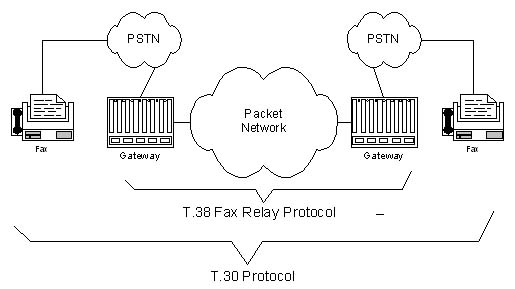
I still haven't figured out how to get free internet or make phone calls mostly because BIG TELECOM is evil and competes against these efforts actively making it probably cost more to set up right now vs using in place traditional physical networks
There is literally no reason why you shouldn't be able to just use a computer in combination with radios to emulate an entire phone network but good luck explaining that to your local ham radio license group that will report you to the government for illegal operation
Originally posted by the man who put it in my hood i'm OTG im an otg im an otg kinda guy
https://www.itnews.com.au/news/uk-ditches-homegrown-covid-19-tracing-app-for-google-apple-model-549442
https://onezero.medium.com/googles-geofence-warrants-face-a-major-legal-challenge-ac6da1408fba
https://www.forbes.com/sites/sergeiklebnikov/2020/06/17/20-year-old-robinhood-customer-commits-suicide-after-seeing-a-730000-negative-balance/#2e3a8a1a5928
https://www.blacklistednews.com/article/77242/irs-says-it-bought-in-to-location-database-for-millions-of-us-cellphones-to-track-tax-crime.html
https://www.flir.com/discover/public-safety/thermal-imaging-for-detecting-elevated-body-temperature/
https://movitherm.com/knowledgebase/coronavirus-screening-for-elevated-body-temperature/
https://www.forbes.com/sites/daveywinder/2020/06/20/have-apple-and-google-suddenly-uploaded-a-covid-19-tracking-app-to-your-phone-android-iphone-exposure-notification-contact-tracing/#b41b11360545
https://www.cnet.com/google-amp/news/prop-24-passes-in-california-pushing-privacy-rights-to-the-forefront-again/
https://www.eff.org/deeplinks/2020/11/police-will-pilot-program-live-stream-amazon-ring-cameras
Originally posted by ☆$P₳C3🐏🌟👍👌🏻꒰⌐■ω■꒱👍🏿🪐$H33P🐑🌛 I'm not familiar with any of these people but yeah IF YOU DonT LIKE IT JUST BUILD YOUR OWN WEB SERVER GOSH IT"s NOT THAT HARD
do like the BBS'ers or fediverse. OTG off the grid. They can only censor and ban you off THEIR networks, no laws against starting your own internet/intranet
https://sizeof.cat/post/lainring/
https://en.wikipedia.org/wiki/GNUnet
https://niggasin.space/thread/82741 -
2024-10-06 at 6:34 PM UTC
Originally posted by Fluttershy Theres really no point when online encrypted communications are so easy to use and readily available.
Radio signals can be tracked, listened in on, or transmitted over if you don't know what you're doing and most people don't. Not to mention, at least here in the US there are many HAM enthusiasts who are so old and ornery and have so much time on their hands they make speedy parker look young again, who can and will hunt you down and report you to the authorities for improper use of equipment.
Plus I'm sure any criminal organization (or any organization) probably isn't exclusively using radio signals for communication, it's likely just used to subsidize other methods of short distance communications (I.E. sensitive information is still likely communicated through encrypted messaging software)
With a radio you already know anybody could be listening so anything sensitive would be coded or said in person. On a phone, with all your Imessages probably being forwarded to some FBI office, people have a false sense of security. And a radio transmits when you transmit. It's not constantly communicating with cell towers and there is nothing to uniquely identify it. To be located on a radio people have to get your signal from multiple locations and triangulate it assuming you're just sitting in one place. Cell towers can do this automatically, assuming they even need to and there isn't some spyware or hardware level shit that can exploit GPS without you turning it on. You can also change frequency whenever you want to, and nobody could legally jam the open channels I don't think anyway. -
2024-10-06 at 6:53 PM UTC
-
2024-10-06 at 6:59 PM UTCI use fax to fax
-
2024-10-06 at 7:34 PM UTCI'm hard rn
-
2024-10-06 at 7:54 PM UTChttp://www.spice-center.org/
http://www.spice-center.org/jie-special-issue/
www.jie-online.org
The main research goals of SPICE are:
The design of space protocols that can dynamically adapt to topology changes and communications anomalies, achieving high-rate of data transmission, even in deep-space missions.
The interoperability between different communication protocols, e.g. protocols used by ESA and NASA.
The dynamic and optimized dissemination of space data to interested institutes and organizations.
The utilization of space communications for terrestrial applications, e.g. emergency situations.
The unification of space and terrestrial internetworking communications.
The deployment of delay tolerant networking for the benefit of terrestrial applications. Examples are energy-saving architectures, social networking, etc. The following users say it would be alright if the author of this post didn't die in a fire!
The following users say it would be alright if the author of this post didn't die in a fire! -
2024-10-06 at 7:56 PM UTC
-
2024-12-15 at 6:42 PM UTCI'm using kilohertz waves to post this right now actually
-
2024-12-15 at 6:49 PM UTCWe could also use smoke signals. I figured if you had to encode a message, you could use a cheap rtl SDR turned into a radio telescope pointed at your friends house, and if the weed deal went through, he could turn his radio on and off twice, followed by turning his TV and computer on and off once. This could mean "mark says alright" and the SDR could pick up the unique RFI plus radio fingerprint associated with the devices turning on and off to receive the message.
Varying the signal strength could also be one way to encode messages. Regular TCP IP traffic through 2.4 GHz could be modulated so it looks normal to anyone not analyzing it with an SDR, but to the person with the SDR, they can find a hidden message in it.
Other than that niggerism -
2024-12-15 at 8:12 PM UTC
Originally posted by 6835378gjjsjs We could also use smoke signals. I figured if you had to encode a message, you could use a cheap rtl SDR turned into a radio telescope pointed at your friends house, and if the weed deal went through, he could turn his radio on and off twice, followed by turning his TV and computer on and off once. This could mean "mark says alright" and the SDR could pick up the unique RFI plus radio fingerprint associated with the devices turning on and off to receive the message.
Varying the signal strength could also be one way to encode messages. Regular TCP IP traffic through 2.4 GHz could be modulated so it looks normal to anyone not analyzing it with an SDR, but to the person with the SDR, they can find a hidden message in it.
Other than that niggerism
You jest but SDR's can listen to anything. Even encrypted shit can alert you to the presence of certain people and possible locations. Like NATO uses FM but lower ranges than commercial radios would pick up.
And your phone basically is a radio and cell towers are repeaters. The difference is that you know anybody could be listening and adapt the conversation. Some guy told me felons couldn't get a licence but I don't think any felon who planned on using it for anything illegal would want one. -
2024-12-15 at 8:25 PM UTC
Originally posted by Cowboy2013 You jest but SDR's can listen to anything. Even encrypted shit can alert you to the presence of certain people and possible locations. Like NATO uses FM but lower ranges than commercial radios would pick up.
And your phone basically is a radio and cell towers are repeaters. The difference is that you know anybody could be listening and adapt the conversation. Some guy told me felons couldn't get a licence but I don't think any felon who planned on using it for anything illegal would want one.
Felons in Japan aren't even allowed to own cell phones.
The phone can be hacked like a raspberry pi when you force it to transmit from the GPIO pins,but it's not a clean transmission if you're trying to use frequency ranges it's not designed for.
Also Army Intel said you're a gifted hacker... C++ I'm guessing mostly eh...
Well, you could probably come up with some sort of implementation but you're probably busy usually doing whatever it is leet haxxors do -
2024-12-15 at 8:26 PM UTCItt too many wordsThe following users say it would be alright if the author of this post didn't die in a fire!
-
2024-12-16 at 12:02 AM UTC
Originally posted by Cowboy2013 With a radio you already know anybody could be listening so anything sensitive would be coded or said in person. On a phone, with all your Imessages probably being forwarded to some FBI office, people have a false sense of security. And a radio transmits when you transmit. It's not constantly communicating with cell towers and there is nothing to uniquely identify it. To be located on a radio people have to get your signal from multiple locations and triangulate it assuming you're just sitting in one place. Cell towers can do this automatically, assuming they even need to and there isn't some spyware or hardware level shit that can exploit GPS without you turning it on. You can also change frequency whenever you want to, and nobody could legally jam the open channels I don't think anyway.
Coded with what? Whats the key? How is that shared?
Shouldnt assume meeting in person, otherwise, just meet in person.
An actor can maybe impersonate another person.
There are many solutions available for E2E communication.
No reason to use Imessages, those radio are probably also recorded.
Just get GrapheneOS, and choose the E2E solution you want.
https://grapheneos.org/ -
2024-12-16 at 1:15 AM UTC
Originally posted by TAP WATER ENJOYER Coded with what? Whats the key? How is that shared?
Shouldnt assume meeting in person, otherwise, just meet in person.
An actor can maybe impersonate another person.
There are many solutions available for E2E communication.
No reason to use Imessages, those radio are probably also recorded.
Just get GrapheneOS, and choose the E2E solution you want.
https://grapheneos.org/
he means talking in code not encryption
I wouldn't trust any modern smartphone not to be backdoored at the driver/firmware level -
2024-12-16 at 1:24 AM UTC
-
2024-12-16 at 1:50 AM UTCtv killed the radio star ....
-
2024-12-16 at 3:47 AM UTCi only use nintendo pictochat to have any incriminating conversations. all other methods of conversation have been compromised by US intellegence.

